Uber reportedly suffered another massive security incident last week. Here is what it means for your business:
Bad actors continue to cause mass chaos for businesses of all industries and sizes following Friday’s news about Uber’s latest breach. This is Uber’s second reported cybersecurity incident since its 2016 data breach and subsequent cover-up. In this blog, we will discuss what likely happened and the ways you can prevent attacks like this from happening to your business.

What we know about the Uber data breach
According to ZDNet, “On Thursday a hacker was believed to have breached multiple internal systems, with administrative access to Uber’s cloud services including Amazon Web Services (AWS) and Google Cloud (GCP).” The article went on to quote a security engineer from Yuga Labs, who corresponded with the hacker and said, “This is a total compromise from what it looks like.”
The said hacker told The New York Times that he had sent a text message to an Uber worker claiming to be a corporate information technology person. “The worker was persuaded to hand over a password that allowed the individual to gain access to Uber’s systems, a technique known as social engineering.”
If a large company like Uber is experiencing multiple hacking instances, what can that mean for your business? Social engineering is a commonly used tactic and cyber criminals are not discriminating by size or industry. A 2018 cybersecurity report said, 67% of companies with fewer than 1,000 employees have experienced a cyberattack, and 58% have experienced a breach. So do not think because you are not a large company you are not a target. In fact, your business is seen as a bigger target for many criminals. This is because large enterprises typically have a large budget for a cybersecurity team and expensive cybersecurity tools in place, where most SMBs (small to mid-sized businesses) are left vulnerable.
Could your company afford an error like this one?
Regardless of your industry or company size, your organization stores data at many levels. Personal information, credit card information, and intellectual property. None of this data is immune to a malicious cyber-attack.
An IBM (International Business Machines) report states that the cost of a data breach in 2021 was $4.24 million. That is the highest average total cost in the 17-year history of the IBM data breach cost report. A simple mistake could cost your company money, time, and your reputation. In Uber’s case, this data breach does not just affect the people working for Uber at a corporate level. This breach could affect millions of drivers, and riders who rely on the rideshare platform to get to and from their destinations.
The importance of cybersecurity training
Your employees are your first line of defense when it comes to cybersecurity. And human error accounts for 82% of data breaches. If you are not doing anything to train your employees in cybersecurity, you are putting your business at risk of a cyber-attack.
Plus, Russia’s invasion of Ukraine is causing concern around the world with threats of impact on organizations including malicious cyber activity against the US (United States). CISA (Cybersecurity & Infrastructure Security Agency) and the Department of Homeland Security issued warnings earlier this year that “every organization in the US is at risk from cyber threats.”
Read more Potential Threat of US Cyber Attack
Steps you can take to prevent yourself from a cyber attack
Some of the first steps you can take to prevent your business from falling victim to an attack like this one is training your employees. Even the most basic cybersecurity principles could protect your company from serious loss.
At CRI Advantage, we offer User Training as part of our cybersecurity services. Keep your team aware of the latest social engineering trends and teach the best IT (Information Technology) practices to prevent cyber-attacks. Some of the benefits of our User Training Module include custom email phishing campaigns and practice social engineering phone calling to test your employee’s knowledge of phishing. A reporting feature is also included to see which employees are most at risk based on performance during testing.
To learn more about our cybersecurity services contact us here or uncover the strengths and weaknesses of your cybersecurity program on your own by filling out our free cybersecurity blueprint.
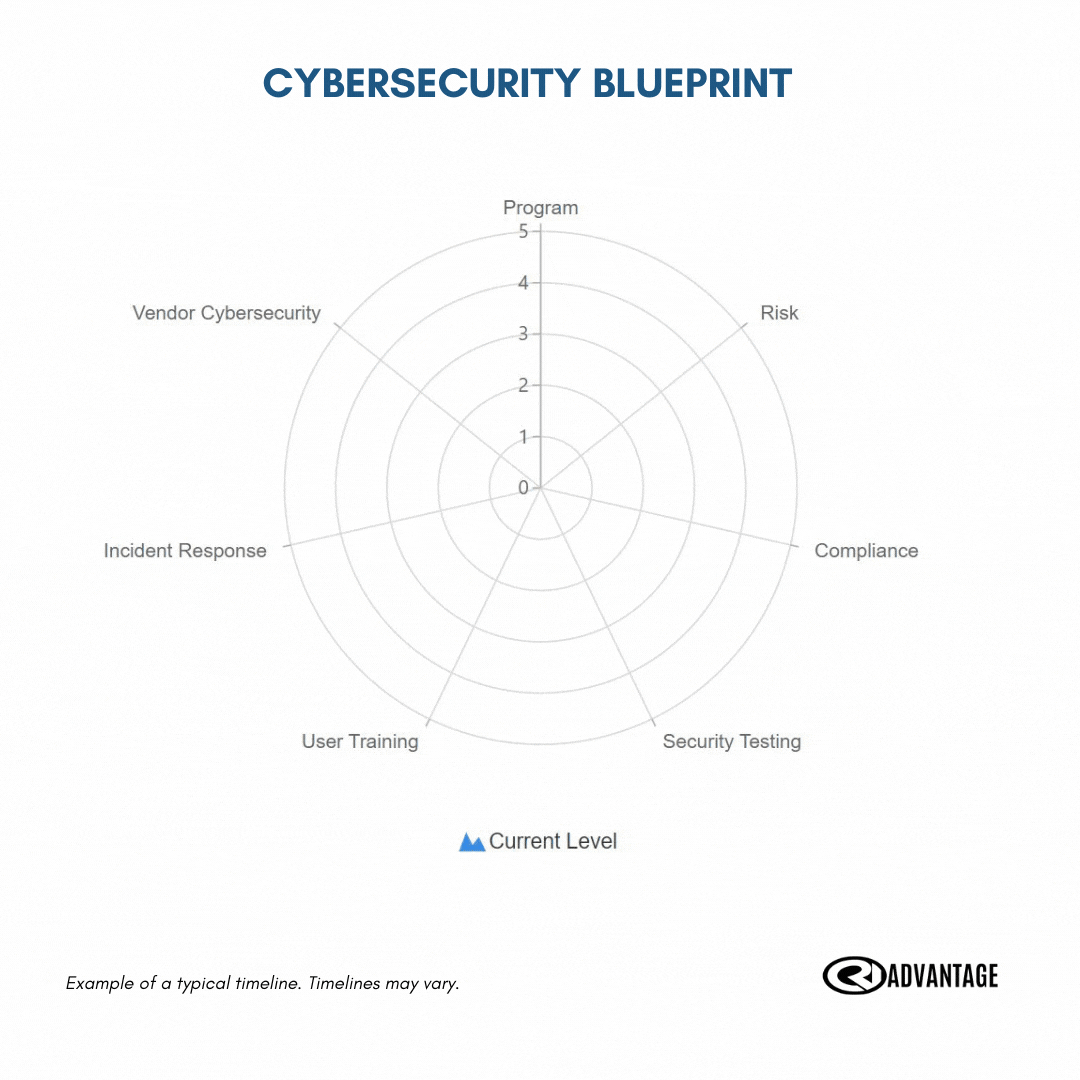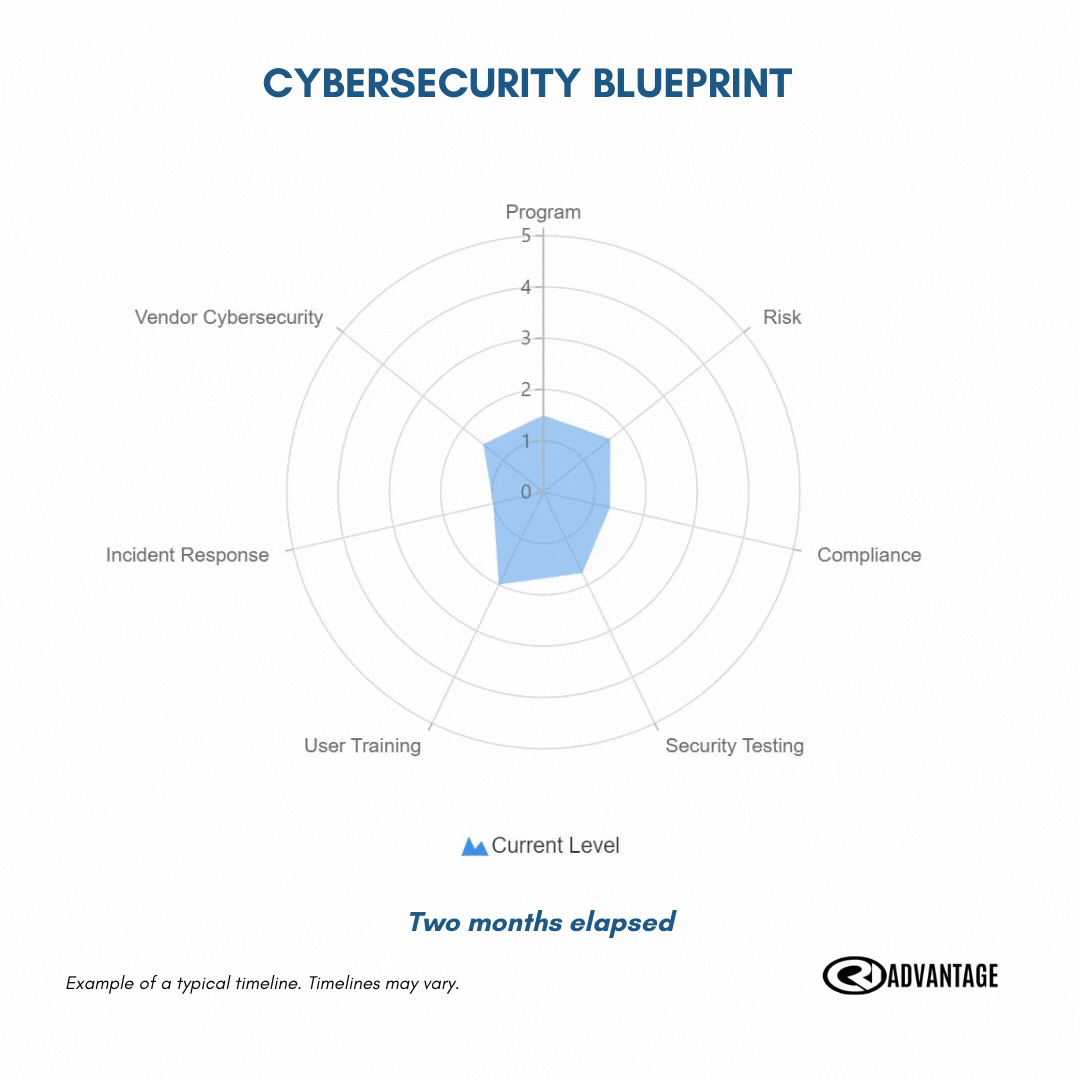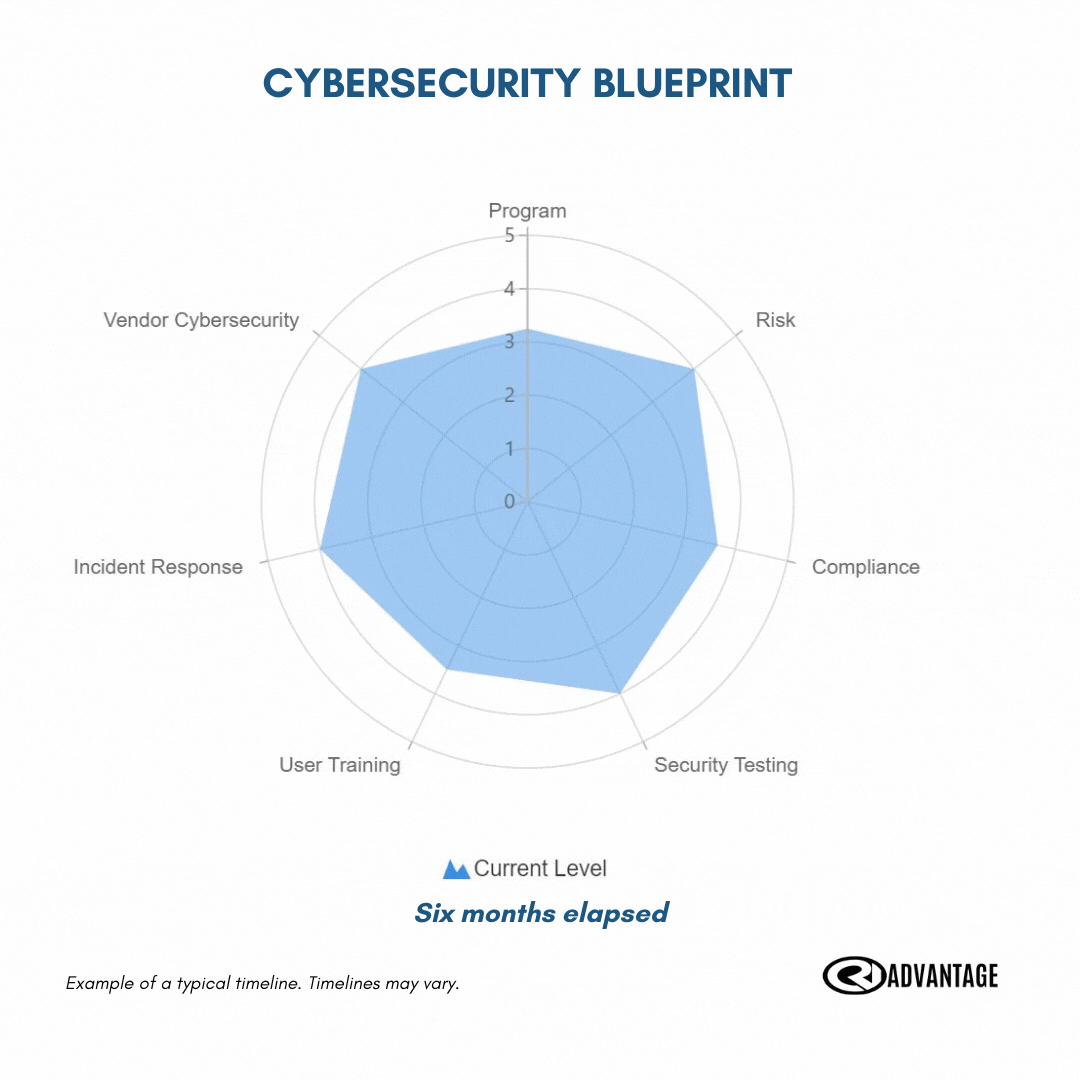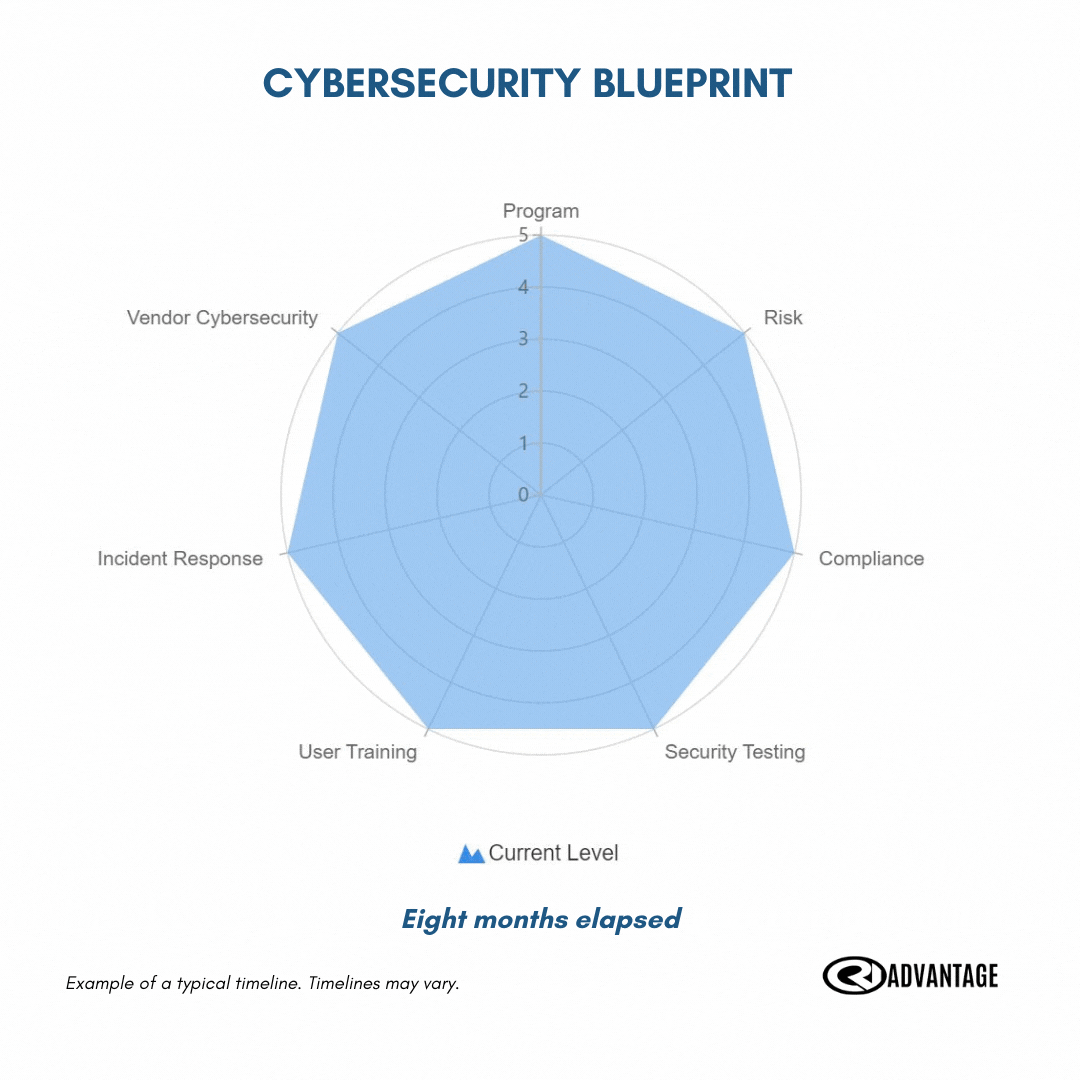
The first step: complete your cybersecurity blueprint exercise
Uncover the strengths and weaknesses of your current cyber efforts.